Post-quantum glossary
Post-quantum cryptography terms can be confusing. Since we have a series of PQC articles on the way, let us clarify some of them to prevent you from getting lost in the forest of post-quantum glossary.
Quantum cryptography vs post-quantum cryptography
Very common confusion point is between quantum cryptography and post-quantum cryptography, so let us start with it.
Quantum cryptography builds on top of laws of quantum physics that have specific properties not available to the classical computers. Therefore, quantum cryptography works only with quantum devices and cannot be realised solely on classical computers.
The most common example of quantum cryptography is quantum key distribution (or QKD). This technology utilises a special quantum channel through which qubits (quantum bits of information) travel to their destination. QKD allows communicating parties to establish a secret key that can be later used to exchange encrypted messages. QKD requires specific and costly infrastructure to be set up, which makes adoption of the technology more resource-consuming.
Due to the properties of quantum mechanics, information sent over the quantum channel cannot be copied. This is a compelling property of the system guaranteeing that the attacks, where adversary listens in on the communication (eavesdropping), can be detected. On the other hand, sensitivity to such attacks has a downside of being more vulnerable to the denial-of-service attacks, where the adversary aims to stop system from functioning. Additionally, there is a caveat in making QKD work for longer distances (over 200 km): one needs to set up multiple trusted nodes on the path.
Post-quantum cryptography works on classical computers and does not require any specific equipment. Underlying hard mathematical problems are what set it apart from pre-quantum cryptography.
Factorisation and discrete logarithm problems are the basis of pre-quantum cryptographic algorithms and are vulnerable to quantum attacks. There are no known quantum attacks for mathematical problems that are the basis of post-quantum cryptographic algorithms, such as learning with errors and short integer solution.
Post-quantum cryptography offers functionality for wider range of applications — key establishment, authentication, encryption, etc. Since post-quantum cryptography algorithms work on classical computers, those can be implemented and tested more easily. Furthermore, the standards for post-quantum cryptography are already being developed and published, making it possible to build interoperable solutions.
Additionally, post-quantum cryptography offers possibility to safeguard more cryptographically complicated applications like Internet voting and SplitKey authentication and signing.
Is the number of qubits enough?
Qubit (quantum bit) is a basic unit of quantum information, like bits for classical computers. Number of qubits is frequently used to measure the progress of quantum technology, and thus we are nearing the period during which we need to switch to post-quantum cryptography. This is not the only property that should be considered.
Imagine, you are trying to prepare the most delicious cake for the Worldwide Cake Competition. Just having the most powerful oven that bakes perfectly is not enough. You should also:
- select proper ingredients for you cake — the ones that are seasonal, fresh and taste the best (selecting what to build qubits from);
- figure out the best recipe — start with some basic recipe and add your magic ingredients (there are known quantum algorithms that can be further optimised);
- do the tasting and quality assurance — once the cake is ready, you need to make sure that it is properly baked, cream is perfectly whipped and decorations are in place. Of course, some errors could happen in the process, this is the place where those should be fixed (developing error-correction strategy);
- figure out and maintain optimal temperature – baking process itself can be complicated and the right temperature can be crucial to receive the expected result (selecting the architecture, how to connect qubits with each other);
Just as baking is a more complicated process than it may seem, so has the quantum computing development many more layers to it that go beyond just measuring the number of qubits. Therefore, news about “having 3000 qubit quantum computer” does not necessarily mean that we are closer to breaking pre-quantum cryptographic algorithms.
Post-quantum cryptography standardisation and migration
Standardisation of post-quantum cryptography was initiated by the US National Institute of Standards and Technology (NIST) in 2016. The primary goal of the project was to standardise post-quantum key establishment mechanisms and digital signature schemes. Currently, there are standard drafts for the schemes that were chosen through the careful selection process.
The table below shows soon-to-be standardised post-quantum alternatives to the commonly used pre-quantum cryptographic algorithms, which are not secure against quantum computer attacks.
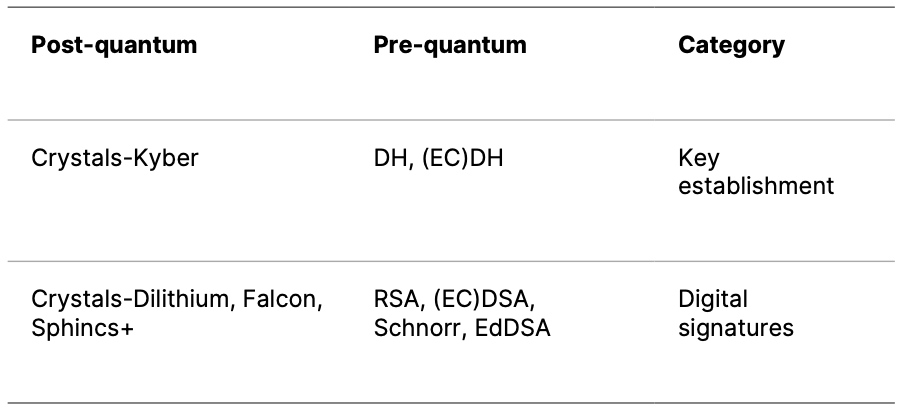
Moreover, there are additional standardisation rounds for key establishment and digital signature schemes to add more variety to the selected schemes.
The goal of post-quantum migration process is to plan and execute the switch of systems from traditional cryptographic algorithms to the ones secure against quantum computer attacks. Since different systems have different purposes, requirements, use-cases and constrains, migration process is unique for each of the systems.
Hybrid mode
You may have encountered term “hybrid mode” when reading about migration process. Since post-quantum algorithms are not considered mature enough to be used as a standalone solutions, it is considered to be a better option to use post-quantum and pre-quantum cryptography simultaneously.
The idea behind this is that if one of the schemes appears to be broken or vulnerable to some attacks, the other scheme will be enough to guarantee security for the user’s information. Intuitive example would be locking your bicycle with two different locks, then it would not be enough for the robber to break just one lock, both locks should be broken for the successful robbery.
