Some 20 years ago Bruce Schneier warned against creating your own cryptographic algorithms at home. The original story was titled "Memo to the Amateur Cipher Designer". The popularity of the topic has not fallen since then, and the Google search "Never roll your own encryption" will still result in multiple hits.
Without paraphrasing Mr Schneier, it could be said that cryptography is too research intensive to be excercised as a hobby. It takes some 10 years for a dedicated cryptographer to grow up in a conditioned environment - having research fellows to discuss problems with, often visiting international conferences etc. The beginners are prone to make these two types of errors - either inventing something "new" that would be too easy to break mathematically or being unaware of proper implementation tricks - so they forget to wipe the used variables from memory and program the algorithm in a way that the power consumption of the processor will reveal the private key.
A well kept secret around the information security industry is that cryptography is not the only research-intensive domain. Whether we talk about the authentication and identity sector or about perimeter protection, you probably should not attempt these at home. The reason is simple - scientific thought on these vital topics descend back to 1970's and in some rare cases even to 1950's.
One of the most ancient approaches was the "Defense in depth" that one can admire on the All.Net web page. In 2004, the term BYOD - Bring Your Own Device - appeared, obscuring the previous clear understanding about the perimeter - an imaginable line surrounding our valuable assets from the hostile Internet.
Further, in 2009, a concept of "The Möbius Defence" was published stirring up the security world. What Peter Herzog actually told us was that an enterprise have to "mud the waters", interleave the real resources by the honeypots and thus stretch the attack surface up to the cosmic size capable to exhaust any adversary. Or as it is often said in Estonia, to escape from a bear, you do not need to outrun the bear, you just need to run faster than your friend.
The security landscape is complex and is affected by multiple factors. Is it possible to take all these into account and calculate our success mathematically? Ideed, there is an interesting scientific direction dealing with the attack trees. It is probably easier to demonstrate what an attack tree is:
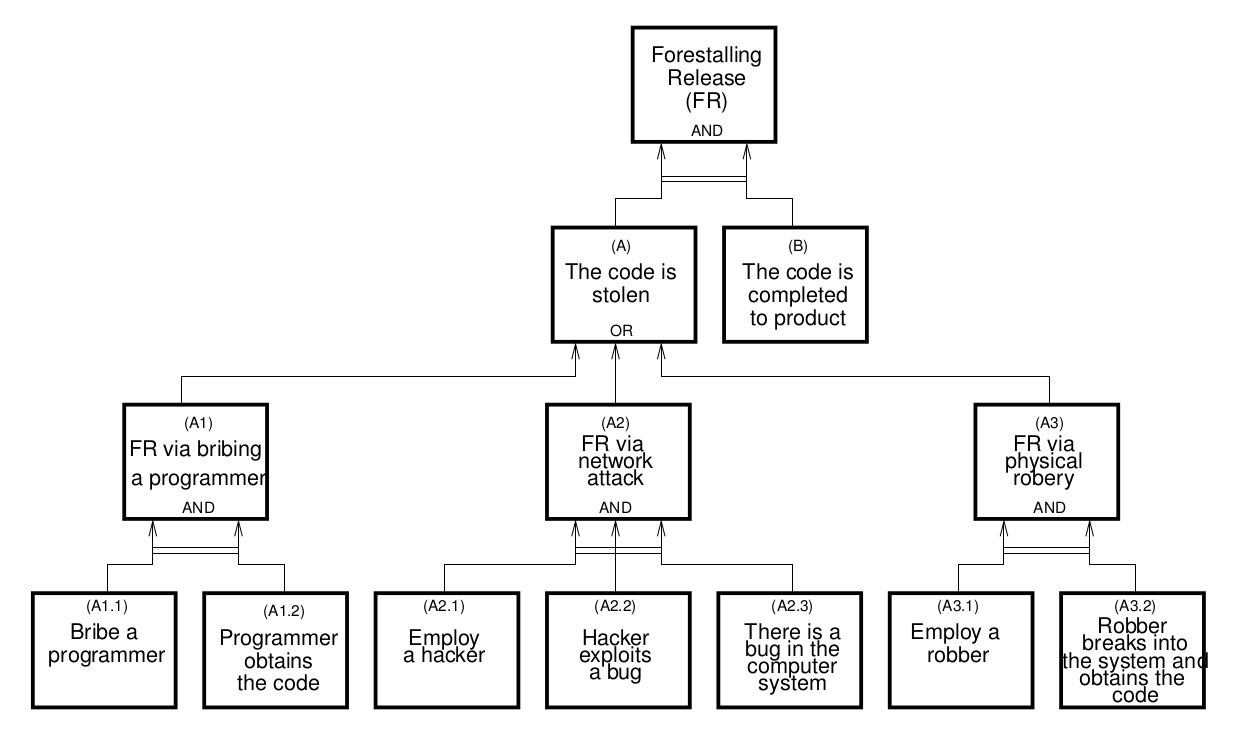
To calculate what the blacbeetle has in mind, as we like to say in Estonian, one has to think like an adversary. It might look like a funny computer game, but in fact these days the models and formulas,or to put it otherwise, mathematical ratiocinations are creating the distinction between the victory and defeat. With stating it, we are back where we started from. It's probably wise to avoid creating security systems from scratch, at home as an amateur, ignoring the half century long scientific research in the area.
Here at Cybernetica we are not amateurs. We have our own Information Security Research Institute - a luxury that few information security companies can afford. Our pledge is - supported by our scientists we are able to create better solutions than someone trying to leave the science out of the security game.
Published by Anto Veldre