UXP team knows how important it is that electronic signatures in the digital society are strong and legitimate. In UXP version 1.21 we have improved the support for signature creation devices to give users the choice for even higher security and compliance. This means that UXP security server covers cases when signing keys must be stored on an external device for additional protection. For a better user experience, managing signature devices is now done in security server's user interface.
Cybernetica's UXP® (Unified eXchange Platform) enables connecting different databases and information systems over public internet with the end goal of creating a trusted digital society for citizens and organisations. European Union's regulation legislation for electronic IDentification, Authentication and trust Services (eIDAS) requires signature creation devices (e.g HSMs, USB tokens) for strong key management and for creating qualified electronic signatures. Thus, UXP members can now create qualified digital signatures according to eIDAS - which is important both in EU and in other countries where governments have adopted similar norms.
Key protection and improvements in UXP 1.21
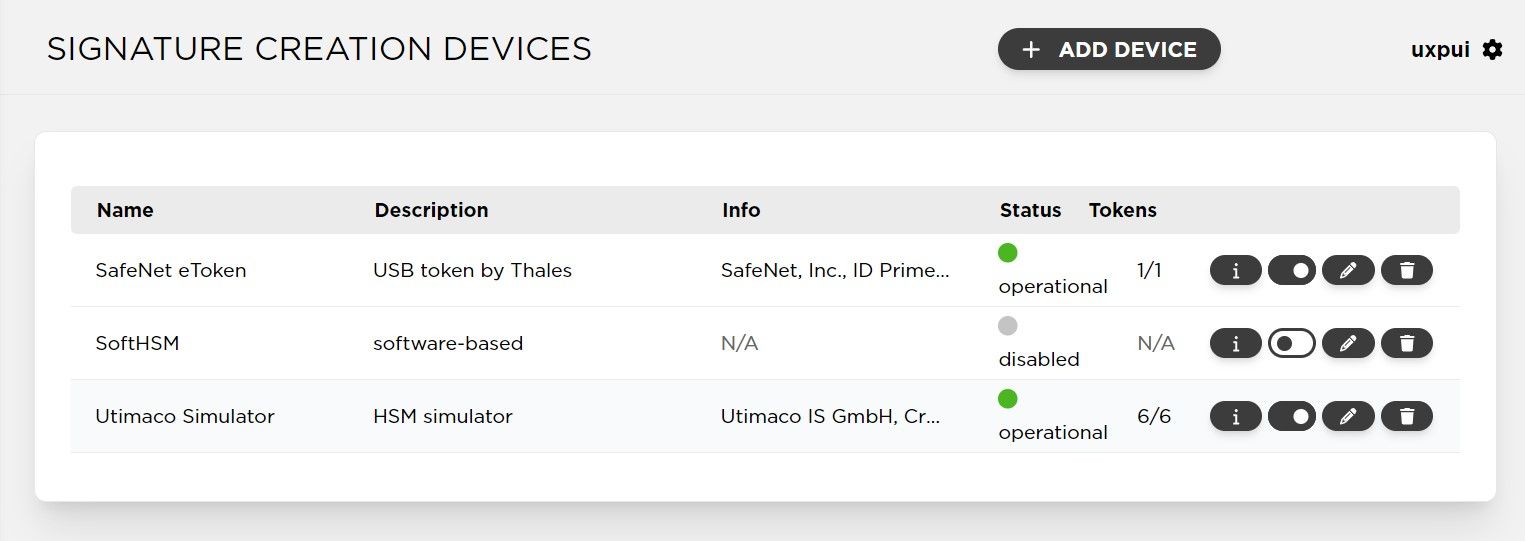
UXP's security server software uses separate keys for internal TLS protocol, authentication and electronic signatures. UXP works well and provides security also without HSMs or external tokens. In this case, security server stores cryptographic keys on a software-based token (encrypted container) that is protected with a PIN. If it is required to use external signature devices in UXP instance then only signing keys can be stored on such device. Other keys remain on the software token. To be connected to the security server the signature creation device must have a PKCS#11 interface which is a standard API for cryptographic devices.
Signing keys must be created through the security server UI, this process is the same for both hardware-based and software based keys. Security server has been tested and confirmed to work with nShield Connect HSM by Entrust. Other HSMs with standard PKCS#11 interface may also work but specific devices by other manufactures will be tested per client needs. In security server UI, signature creation devices are to be found on a separate page. The UI got other improvemens as well. Now server certificates are on a separate page and objects on tokens (keys, certificates, CSRs) are better distinguishable. Also, message exchange performance has been improved in UXP 1.21 by up to 25%.
Next steps and a peek into the roadmap
We always recommend our clients to upgrade UXP software to the newest version to get the best user experience and ensure the security of the system. For the ones who need to start using HSMs there is a guide available on connecting devices and managing tokens and keys. If there are questions about the specific setup of signature devices then we ask to contact us to discuss it in more detail.
One of the next items in UXP roadmap is to simplify managing organisations and user accounts in the security server. We plan for a new security server operation model where a server owner organisation could easily host other organisations who do not wish to do the full security server management themselves. Concurrently, every organisation would see only their own resources like keys, tokens and web sevices. We have wondered, what if UXP member organisations would have the flexibility to delegate the security server owner as much rights as they see fit. And what if all user accounts could be conveniently managed in the server GUI. In the following months, the team will be discovering solutions in these fields.
