“It is important to initiate a routine process for cybersecurity and not just casually.”
The primary tools of office jobs are computers and other smart devices. Instead of working with piles of papers and setting up all meetings in person, a somewhat time-consuming matter, we have the convenience of arranging all of that online. Furthermore, the remote and flexible working arrangements allow people to work from anywhere in the world.
It is safe to say we spend more and more time online – after all, a large part of today’s society’s social life is online, too. Alas, the conveniences of our digitalised lives may come at a cost.
Recently, our Head of Cybersecurity Department Sander Valvas discussed threat management systems in a blog article. “The problem is not the cost of information security management, but lack of skills to implement suitable risk/threat/vulnerability management system(s) and procedures,” he said. To reiterate and discuss the importance of cybersecurity in a firm of any size, we collaborated with out good client Directo in a recent webinar. Rewatch the webinar in Estonian here.
We started off the webinar with some questions and we instantly met with a telling fact – over 50% of respondents said there had been records of cyber incidents at their company. On the other hand, about 30% of respondents did not know if there were any incidents recorded. “It is quite common to not be aware of the incidents, since cyberattackers act covertly and unnoticeably,” commented Directo’s CISO Toomas Oper. When asked what the respondents see as the biggest threats, a noteworthy amount of mentions for human error and ignorance came in. It is great to see that people are acknowledging the most common threats, and that the lack of knowledge is seen as threat, too.
When talking about the most common threats, Toomas Oper noted that phishing schemes are developing rapidly and becoming more and more believable. The most common scheme is someone impersonating a CEO or other management member asking you to click on links, pay invoices or transfer money urgently. More often than not, the emails are written with a sense of urgency. Of course, the best practice is to ignore these emails and simply delete them. Always make sure to double check the sender’s email letter by letter. Living in a country with a complicated language, like us here in Estonia, is also a great giveaway for such phishing emails since they almost always sound unnaturally written.
The centre point of our webinar was a rather simple message – invest into prevention since aftermath of a cyberattack is always more expensive. “For example, if a company happens to fall prey to a cyberattacker and sensitive data is leaked, the company may be facing repercussions of the GDPR, and they may turn out to be costly,” said Oper. In addition to the initial devastating financial consequence, the company may lose its credibility and trustworthiness, which again send the business into a downward spiral. This is of course the worst-case scenario, but not an unlikely one.
So, how should a company begin to navigate towards the right cybersecurity solution? “Firstly, a company should assess its value and choose a solution that is financially optimal and in line with its assets’ worth,” said Sander Valvas, Head of Cybersecurity at Cybernetica. “A good starting point is evaluating the core processes of your company. Say, your company operates with direct sales and relies on ERP software. Imagine you are not able to access it for some period of time, what would happen then?” Valvas continued. Should the company’s work be restricted or it is impossible to operate without the software, it outlines a clear business priority that has to be protected.
Here are some questions a company should think about that help with the asset evaluation:
- Can we operate without our assets?
- What happens if we lose access to the assets?
- How long can we operate without the assets?
- What happens if a stranger gains access to my assets?
- What happens if a stranger is able to modify my assets?
“It is important to initiate a routine process for cybersecurity and not just casually,” said Valvas. As a basic starter, conducting a cyber hygiene training for all employees is a must, as well as being responsible for keeping passwords strong, safe and using multi-factor authentication.
While figuring out the evaluation, it is a good idea to map the threats and possible perpertators.
The threats include:
- Force majeure, such as environmental disasters, technical problems, human errors
- Targeted attacks, such as phishing, DDoS attacks, ransomware, malware, social engineering, threats agains data, internet threats, disinformation, misinformation, supply chain attacks etc
The possible perpetrators include:
- An internal perpetrator, such as an employee or an ex-employee
- A state-level attacker
- An attacker looking for materialistic gains
- Hackers
- A competitor
- An attacker looking for revenge
- Simply casual attackers
And lastly, Valvas suggests to evaluate possible losses:
- Breaking regulations, laws or contracts
- Harm to personal health or wellbeing
- Harm to business operations
- Harm to public image
- Financial losses
Nowadays it is very common to outsource various IT or cybersecurity services in order to save costs and resources, but the risks have to be assessed here, too.
Valvas lists some of the risks that come with subcontractors:
- Lack of control
- Communication errors
- Poor quality of services and software
- Lack of industry knowledge
- Unforeseen expenses
- Lack of experience with distributed teams
- Security breaches and lack of IP protection
On the other hand, there are many notable benefits of subcontractors, such as:
- Cost effectiveness
- Effectivity increase within business operations
- Ability to focus on main priorities
- Access to knowledge and skills
- Increased flexibility to cope with variable business conditions
- Accelerated business launch on the market
“A common misconception with outsourcing is that the subcontractor is responsible for everything. In reality, both the client and the subcontractor hold a divided responsibility over processes,” said Valvas. Microsoft has illustrated this issue well in a following graphic:
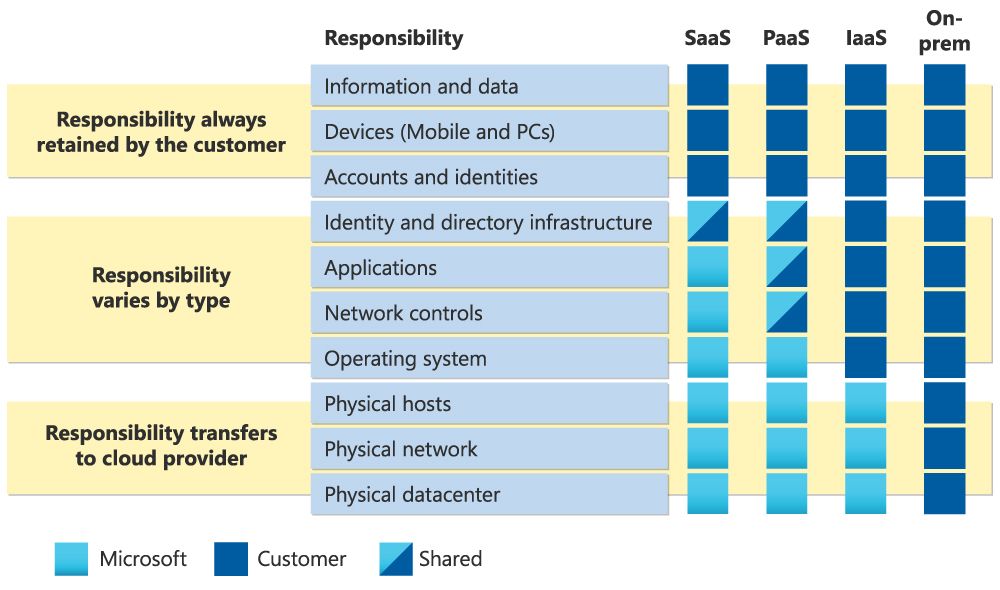
“In conclusion, the most important is to raise employees’ awareness about utilising company’s assets in a correct and a mindful matter. Refrain from using social media on your work computer and be mindful of where you click. Don’t store important assets in cloud drives or on personal accounts,” Valvas concluded.
While on this topic, we suggest reading further about dealing with a cyberattack and how to correctly back up your data to avoid catastrophic losses.
Should you be interested in cybersecurity solutions offered by Cybernetica, learn more here and don’t hesitate to get in touch via the contact form.
